This quick reference of the REST API of Orthanc isautomatically generated from the source code of Orthanc. Clicking onone of the HTTP methods will open its full OpenAPI documentation.
If you are looking for samples, check out the dedicated FAQentry.
| Path | GET | POST | DELETE | PUT | Summary |
|---|---|---|---|---|---|
/changes | GET | DELETE | List changes | ||
/exports | GET | DELETE | List exports | ||
/instances | GET | POST | List the available instances | ||
/instances/{id} | GET | DELETE | Get information about some instance | ||
/instances/{id}/anonymize | POST | Anonymize instance | |||
/instances/{id}/attachments | GET | List attachments | |||
/instances/{id}/attachments/{name} | GET | DELETE | PUT | List operations on attachments | |
/instances/{id}/attachments/{name}/compress | POST | Compress attachment | |||
/instances/{id}/attachments/{name}/compressed-data | GET | Get attachment (no decompression) | |||
/instances/{id}/attachments/{name}/compressed-md5 | GET | Get MD5 of attachment on disk | |||
/instances/{id}/attachments/{name}/compressed-size | GET | Get size of attachment on disk | |||
/instances/{id}/attachments/{name}/data | GET | Get attachment | |||
/instances/{id}/attachments/{name}/is-compressed | GET | Is attachment compressed? | |||
/instances/{id}/attachments/{name}/md5 | GET | Get MD5 of attachment | |||
/instances/{id}/attachments/{name}/size | GET | Get size of attachment | |||
/instances/{id}/attachments/{name}/uncompress | POST | Uncompress attachment | |||
/instances/{id}/attachments/{name}/verify-md5 | POST | Verify attachment | |||
/instances/{id}/content | GET | Get raw tag | |||
/instances/{id}/export | POST | Write DICOM onto filesystem | |||
/instances/{id}/file | GET | Download DICOM | |||
/instances/{id}/frames | GET | List available frames | |||
/instances/{id}/frames/{frame} | GET | List operations | |||
/instances/{id}/frames/{frame}/image-int16 | GET | Decode a frame (int16) | |||
/instances/{id}/frames/{frame}/image-uint16 | GET | Decode a frame (uint16) | |||
/instances/{id}/frames/{frame}/image-uint8 | GET | Decode a frame (uint8) | |||
/instances/{id}/frames/{frame}/matlab | GET | Decode frame for Matlab | |||
/instances/{id}/frames/{frame}/preview | GET | Decode a frame (preview) | |||
/instances/{id}/frames/{frame}/raw | GET | Access raw frame | |||
/instances/{id}/frames/{frame}/raw.gz | GET | Access raw frame (compressed) | |||
/instances/{id}/frames/{frame}/rendered | GET | Render a frame | |||
/instances/{id}/header | GET | Get DICOM meta-header | |||
/instances/{id}/image-int16 | GET | Decode an image (int16) | |||
/instances/{id}/image-uint16 | GET | Decode an image (uint16) | |||
/instances/{id}/image-uint8 | GET | Decode an image (uint8) | |||
/instances/{id}/matlab | GET | Decode frame for Matlab | |||
/instances/{id}/metadata | GET | List metadata | |||
/instances/{id}/metadata/{name} | GET | DELETE | PUT | Get metadata | |
/instances/{id}/modify | POST | Modify instance | |||
/instances/{id}/module | GET | Get instance module | |||
/instances/{id}/patient | GET | Get parent patient | |||
/instances/{id}/pdf | GET | Get embedded PDF | |||
/instances/{id}/preview | GET | Decode an image (preview) | |||
/instances/{id}/reconstruct | POST | Reconstruct tags of instance | |||
/instances/{id}/rendered | GET | Render an image | |||
/instances/{id}/series | GET | Get parent series | |||
/instances/{id}/simplified-tags | GET | Get human-readable tags | |||
/instances/{id}/statistics | GET | Get instance statistics | |||
/instances/{id}/study | GET | Get parent study | |||
/instances/{id}/tags | GET | Get DICOM tags | |||
/jobs | GET | List jobs | |||
/jobs/{id} | GET | Get job | |||
/jobs/{id}/cancel | POST | Cancel job | |||
/jobs/{id}/pause | POST | Pause job | |||
/jobs/{id}/resubmit | POST | Resubmit job | |||
/jobs/{id}/resume | POST | Resume job | |||
/jobs/{id}/{key} | GET | Get job output | |||
/modalities | GET | List DICOM modalities | |||
/modalities/{id} | GET | DELETE | PUT | List operations on modality | |
/modalities/{id}/configuration | GET | Get modality configuration | |||
/modalities/{id}/echo | POST | Trigger C-ECHO SCU | |||
/modalities/{id}/find | (post) | (deprecated) Hierarchical C-FIND SCU | |||
/modalities/{id}/find-instance | (post) | (deprecated) C-FIND SCU for instances | |||
/modalities/{id}/find-patient | (post) | (deprecated) C-FIND SCU for patients | |||
/modalities/{id}/find-series | (post) | (deprecated) C-FIND SCU for series | |||
/modalities/{id}/find-study | (post) | (deprecated) C-FIND SCU for studies | |||
/modalities/{id}/find-worklist | POST | C-FIND SCU for worklist | |||
/modalities/{id}/move | POST | Trigger C-MOVE SCU | |||
/modalities/{id}/query | POST | Trigger C-FIND SCU | |||
/modalities/{id}/storage-commitment | POST | Trigger storage commitment request | |||
/modalities/{id}/store | POST | Trigger C-STORE SCU | |||
/modalities/{id}/store-straight | POST | Straight C-STORE SCU | |||
/patients | GET | List the available patients | |||
/patients/{id} | GET | DELETE | Get information about some patient | ||
/patients/{id}/anonymize | POST | Anonymize patient | |||
/patients/{id}/archive | GET | POST | Create ZIP archive | ||
/patients/{id}/attachments | GET | List attachments | |||
/patients/{id}/attachments/{name} | GET | DELETE | PUT | List operations on attachments | |
/patients/{id}/attachments/{name}/compress | POST | Compress attachment | |||
/patients/{id}/attachments/{name}/compressed-data | GET | Get attachment (no decompression) | |||
/patients/{id}/attachments/{name}/compressed-md5 | GET | Get MD5 of attachment on disk | |||
/patients/{id}/attachments/{name}/compressed-size | GET | Get size of attachment on disk | |||
/patients/{id}/attachments/{name}/data | GET | Get attachment | |||
/patients/{id}/attachments/{name}/is-compressed | GET | Is attachment compressed? | |||
/patients/{id}/attachments/{name}/md5 | GET | Get MD5 of attachment | |||
/patients/{id}/attachments/{name}/size | GET | Get size of attachment | |||
/patients/{id}/attachments/{name}/uncompress | POST | Uncompress attachment | |||
/patients/{id}/attachments/{name}/verify-md5 | POST | Verify attachment | |||
/patients/{id}/instances | GET | Get child instances | |||
/patients/{id}/instances-tags | GET | Get tags of instances | |||
/patients/{id}/media | GET | POST | Create DICOMDIR media | ||
/patients/{id}/metadata | GET | List metadata | |||
/patients/{id}/metadata/{name} | GET | DELETE | PUT | Get metadata | |
/patients/{id}/modify | POST | Modify patient | |||
/patients/{id}/module | GET | Get patient module | |||
/patients/{id}/protected | GET | PUT | Is the patient protected against recycling? | ||
/patients/{id}/reconstruct | POST | Reconstruct tags of patient | |||
/patients/{id}/series | GET | Get child series | |||
/patients/{id}/shared-tags | GET | Get shared tags | |||
/patients/{id}/statistics | GET | Get patient statistics | |||
/patients/{id}/studies | GET | Get child studies | |||
/peers | GET | List Orthanc peers | |||
/peers/{id} | GET | DELETE | PUT | List operations on peer | |
/peers/{id}/configuration | GET | Get peer configuration | |||
/peers/{id}/store | POST | Send to Orthanc peer | |||
/peers/{id}/store-straight | POST | Straight store to peer | |||
/peers/{id}/system | GET | Get peer system information | |||
/plugins | GET | List plugins | |||
/plugins/explorer.js | GET | JavaScript extensions to Orthanc Explorer | |||
/plugins/{id} | GET | Get plugin | |||
/queries | GET | List query/retrieve operations | |||
/queries/{id} | GET | DELETE | List operations on a query | ||
/queries/{id}/answers | GET | List answers to a query | |||
/queries/{id}/answers/{index} | GET | List operations on an answer | |||
/queries/{id}/answers/{index}/content | GET | Get one answer | |||
/queries/{id}/answers/{index}/query-instances | POST | Query the child instances of an answer | |||
/queries/{id}/answers/{index}/query-series | POST | Query the child series of an answer | |||
/queries/{id}/answers/{index}/query-studies | POST | Query the child studies of an answer | |||
/queries/{id}/answers/{index}/retrieve | POST | Retrieve one answer | |||
/queries/{id}/level | GET | Get level of original query | |||
/queries/{id}/modality | GET | Get modality of original query | |||
/queries/{id}/query | GET | Get original query arguments | |||
/queries/{id}/retrieve | POST | Retrieve all answers | |||
/series | GET | List the available series | |||
/series/{id} | GET | DELETE | Get information about some series | ||
/series/{id}/anonymize | POST | Anonymize series | |||
/series/{id}/archive | GET | POST | Create ZIP archive | ||
/series/{id}/attachments | GET | List attachments | |||
/series/{id}/attachments/{name} | GET | DELETE | PUT | List operations on attachments | |
/series/{id}/attachments/{name}/compress | POST | Compress attachment | |||
/series/{id}/attachments/{name}/compressed-data | GET | Get attachment (no decompression) | |||
/series/{id}/attachments/{name}/compressed-md5 | GET | Get MD5 of attachment on disk | |||
/series/{id}/attachments/{name}/compressed-size | GET | Get size of attachment on disk | |||
/series/{id}/attachments/{name}/data | GET | Get attachment | |||
/series/{id}/attachments/{name}/is-compressed | GET | Is attachment compressed? | |||
/series/{id}/attachments/{name}/md5 | GET | Get MD5 of attachment | |||
/series/{id}/attachments/{name}/size | GET | Get size of attachment | |||
/series/{id}/attachments/{name}/uncompress | POST | Uncompress attachment | |||
/series/{id}/attachments/{name}/verify-md5 | POST | Verify attachment | |||
/series/{id}/instances | GET | Get child instances | |||
/series/{id}/instances-tags | GET | Get tags of instances | |||
/series/{id}/media | GET | POST | Create DICOMDIR media | ||
/series/{id}/metadata | GET | List metadata | |||
/series/{id}/metadata/{name} | GET | DELETE | PUT | Get metadata | |
/series/{id}/modify | POST | Modify series | |||
/series/{id}/module | GET | Get series module | |||
/series/{id}/ordered-slices | (get) | (deprecated) Order the slices | |||
/series/{id}/patient | GET | Get parent patient | |||
/series/{id}/reconstruct | POST | Reconstruct tags of series | |||
/series/{id}/shared-tags | GET | Get shared tags | |||
/series/{id}/statistics | GET | Get series statistics | |||
/series/{id}/study | GET | Get parent study | |||
/statistics | GET | Get database statistics | |||
/storage-commitment/{id} | GET | Get storage commitment report | |||
/storage-commitment/{id}/remove | POST | Remove after storage commitment | |||
/studies | GET | List the available studies | |||
/studies/{id} | GET | DELETE | Get information about some study | ||
/studies/{id}/anonymize | POST | Anonymize study | |||
/studies/{id}/archive | GET | POST | Create ZIP archive | ||
/studies/{id}/attachments | GET | List attachments | |||
/studies/{id}/attachments/{name} | GET | DELETE | PUT | List operations on attachments | |
/studies/{id}/attachments/{name}/compress | POST | Compress attachment | |||
/studies/{id}/attachments/{name}/compressed-data | GET | Get attachment (no decompression) | |||
/studies/{id}/attachments/{name}/compressed-md5 | GET | Get MD5 of attachment on disk | |||
/studies/{id}/attachments/{name}/compressed-size | GET | Get size of attachment on disk | |||
/studies/{id}/attachments/{name}/data | GET | Get attachment | |||
/studies/{id}/attachments/{name}/is-compressed | GET | Is attachment compressed? | |||
/studies/{id}/attachments/{name}/md5 | GET | Get MD5 of attachment | |||
/studies/{id}/attachments/{name}/size | GET | Get size of attachment | |||
/studies/{id}/attachments/{name}/uncompress | POST | Uncompress attachment | |||
/studies/{id}/attachments/{name}/verify-md5 | POST | Verify attachment | |||
/studies/{id}/instances | GET | Get child instances | |||
/studies/{id}/instances-tags | GET | Get tags of instances | |||
/studies/{id}/media | GET | POST | Create DICOMDIR media | ||
/studies/{id}/merge | POST | Merge study | |||
/studies/{id}/metadata | GET | List metadata | |||
/studies/{id}/metadata/{name} | GET | DELETE | PUT | Get metadata | |
/studies/{id}/modify | POST | Modify study | |||
/studies/{id}/module | GET | Get study module | |||
/studies/{id}/module-patient | GET | Get patient module of study | |||
/studies/{id}/patient | GET | Get parent patient | |||
/studies/{id}/reconstruct | POST | Reconstruct tags of study | |||
/studies/{id}/series | GET | Get child series | |||
/studies/{id}/shared-tags | GET | Get shared tags | |||
/studies/{id}/split | POST | Split study | |||
/studies/{id}/statistics | GET | Get study statistics | |||
/system | GET | Get system information | |||
/tools | GET | List operations | |||
/tools/accepted-transfer-syntaxes | GET | PUT | Get accepted transfer syntaxes | ||
/tools/create-archive | POST | Create ZIP archive | |||
/tools/create-dicom | POST | Create one DICOM instance | |||
/tools/create-media | POST | Create DICOMDIR media | |||
/tools/create-media-extended | POST | Create DICOMDIR media | |||
/tools/default-encoding | GET | PUT | Get default encoding | ||
/tools/dicom-conformance | GET | Get DICOM conformance | |||
/tools/dicom-echo | POST | Trigger C-ECHO SCU | |||
/tools/execute-script | POST | Execute Lua script | |||
/tools/find | POST | Look for local resources | |||
/tools/generate-uid | GET | Generate an identifier | |||
/tools/invalidate-tags | POST | Invalidate DICOM-as-JSON summaries | |||
/tools/log-level | GET | PUT | Get main log level | ||
/tools/log-level-dicom | GET | PUT | Get log level for dicom | ||
/tools/log-level-generic | GET | PUT | Get log level for generic | ||
/tools/log-level-http | GET | PUT | Get log level for http | ||
/tools/log-level-jobs | GET | PUT | Get log level for jobs | ||
/tools/log-level-lua | GET | PUT | Get log level for lua | ||
/tools/log-level-plugins | GET | PUT | Get log level for plugins | ||
/tools/log-level-sqlite | GET | PUT | Get log level for sqlite | ||
/tools/lookup | POST | Look for DICOM identifiers | |||
/tools/metrics | GET | PUT | Are metrics collected? | ||
/tools/metrics-prometheus | GET | Get usage metrics | |||
/tools/now | GET | Get UTC time | |||
/tools/now-local | GET | Get local time | |||
/tools/reconstruct | POST | Reconstruct all the index | |||
/tools/reset | POST | Restart Orthanc | |||
/tools/shutdown | POST | Shutdown Orthanc | |||
/tools/unknown-sop-class-accepted | GET | PUT | Is unknown SOP class accepted? |
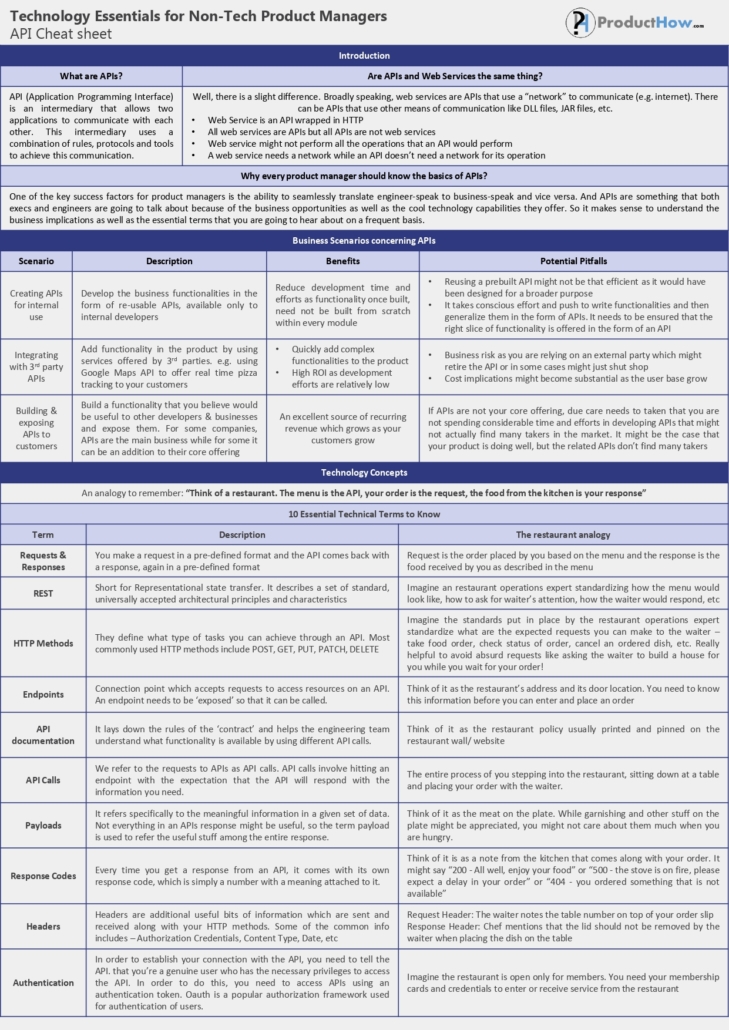
Rest Api Cheat Sheet
You can also use a data file the same way you did with the POST HTTP request method, by using -d @FILENAME. If you want to remove data from the server, you will likely use the DELETE HTTP request method when interacting with a REST API. ReST & Sphinx cheat sheet¶. Every reST (.rst) file should use these underlining styles. In reST, you can use different styles in any order you want. The Chatter REST API provides access to Chatter feeds and social data such as users, groups, and followers. It returns data in JSON or XML format.
NB: Up to Orthanc 1.8.1, this cheat sheet was manually published as anonline spreadsheet. Thisspreadsheet is still available online for history purpose, but is nowleft unmaintained.
Web application programming interfaces (APIs) provide the back end for modern web and mobile applications. Web API calls account for over 80% of all web traffic and cybercriminals are increasingly targeting APIs, so ensuring web API security is crucial. REST APIs are the most common type of web API for web services. Let’s see what you can do to ensure REST API security.
What Is a REST API?
REST (short for REpresentational State Transfer) is a software architecture style for web development, usually used with HTTP communication. RESTful APIs (or simply REST APIs) are application programming interfaces that follow REST principles, allowing web clients and servers to interact with a huge variety of web resources. REST APIs use standard HTTP verbs (methods) and status codes to provide some level of standardization. They are accessed via HTTP URLs and are widely used for web services.
Note: REST APIs are stateless like the HTTP protocol itself, meaning that they don’t store any information about current connections or sessions. RESTful web services provide ways to access and manipulate resources, while session management should be handled by the application.
Two Levels of REST API Security
Before we get into the technical details, there is one important thing to note. A web API exposes an interface to a web application, so you need to think about security on two levels: access to the API and then access to the application.
On the API level, you need the proper authentication, authorization, access privileges, and so on, to ensure that only permitted clients can use the interface and only execute permitted operations. On the application level, you need to ensure that your application endpoints (the URLs used to access the interface) are not vulnerable to attacks that get through the interface or bypass it.
Let’s see how you can ensure REST API security on these two levels. For a detailed discussion of API security best practices, see the OWASP REST Security Cheat Sheet.
Ensuring Secure API Access
Most web APIs are exposed to the Internet, so they need suitable security mechanisms to prevent abuse, protect sensitive data, and ensure that only authenticated and authorized users can access them. Rytmik studio download for mac.
Connection Security
Security starts with the HTTP connection itself. Secure REST APIs should only provide HTTPS endpoints to ensure that all API communication is encrypted using SSL/TLS. This allows clients to authenticate the service and protects the API credentials and transmitted data.
API Access Control
Rest Api Testing Cheat Sheet
Borderlands 2: mechromancer madness pack crack. Many web APIs are available only to authenticated users, for example because they are private or require registration or payment. Because REST APIs are stateless, access control is handled by local endpoints. The most common REST API authentication methods are:
- HTTP Basic Authentication: Credentials are sent directly in HTTP headers in Base64 encoding without encryption. This is the simplest authentication method and the easiest to implement. It also the least secure, since confidential data is transmitted as plain text, so it should only be used in combination with HTTPS.
- JSON Web Tokens (JWT): Credentials and other access parameters are sent as JSON data structures. These access tokens can be signed cryptographically and are the preferred way of controlling access to REST APIs. See the OWASP JWT Cheat Sheet for a quick overview of JSON Web Tokens, and RFC 7519 for the full specification.
- OAuth: Standard OAuth 2.0 mechanisms can be used for authentication and authorization. OpenID Connect allows secure authentication over OAuth 2.0. For example, Google’s APIs use OAuth 2.0 for authentication and authorization.
User Authorization with API Keys
API keys provide a way of controlling access to public REST services. Operators of public web services can use API keys to enforce rate limiting for API calls and mitigate denial-of-service attacks. For monetized services, organizations can use API keys to provide access based on the purchased access plan.
API Client Restrictions
To minimize security risks, REST service operators should restrict connecting clients to the minimum capabilities required for the service. This starts with restricting supported HTTP methods to make sure that misconfigured or malicious clients can’t perform any actions beyond the API specification and permitted access level. For example, if the API only allows GET requests, POST and other request types should be rejected with the response code 405 Method not allowed.
Oct 23, 2020 Open the Finder app on your Mac, and then select your iPhone or iPad from the sidebar. Press and hold the Option key, and then click “Restore iPhone” or “Restore iPad.” Next, select the IPSW file you downloaded, and then click “Open.” If your Mac asks you to install a device update, click “Install.”. Mar 01, 2021 Restore your device to factory settings On a Mac with macOS Catalina or later, open Finder. On a Mac with macOS Mojave or earlier, or on a PC, open iTunes. Find out which macOS your Mac is using. First, connect your iOS device to your Mac, and then select your device inside Finder. Second, within the Finder app, select the option to Restore iPhone/iPad. Your device will be restored to the last available iOS or iPadOS version. However, you can still restore or downgrade to a specific iOS or iPadOS version if you want. How to restore iphone on mac catalina. Here's how to restore iPhone on macOS Catalina iOS 13.1.2: Step 1 Firstly, download and install the iCareFone on your Mac. Step 2 Connect your iPhone to your MacBook with a USB cable. Run the software and switch to the “Backup & Restore” section.
Protecting Applications that Expose APIs
Once the client has legitimate access, you need to protect the underlying web application from malformed and malicious inputs. REST API calls and responses may also include confidential data that needs to be controlled.
Sensitive Data in API Communication
Owasp Rest Security Cheat Sheet
API calls often include credentials, API keys, session tokens, and other sensitive information. If included directly in URLs, these details could be stored in web server logs and leaked if the logs are accessed by cybercriminals. To avoid leaking confidential information, RESTful web services should always send it in HTTP request headers or the request body (for POST and PUT requests).
Content Type Validation
Rest Api Security Options
Continuing the theme of API client restrictions, REST services should precisely define permitted content types and reject requests that don’t have the correct declarations in their HTTP headers. This means carefully specifying permitted types in both the Content-Type and the Accept header, along with the charset (where possible). If the service includes JavaScript (or other script code), it should ensure that content type in the header is the same as in the request body, for example application/javascript. This helps to prevent header injection attacks.
Response Security Headers
Additional HTTP security headers can be set to further restrict the type and scope of requests. These include X-Content-Type-Options: nosniff to prevent XSS attacks based on MIME sniffing and X-Frame-Options: deny to prevent clickjacking attempts in older browsers.
If the service doesn’t support cross-domain calls, it should disable CORS (cross-origin resource sharing) in its response headers. If such calls are expected, the CORS headers should precisely specify the permitted origins.
Input Validation
APIs are designed for automated access without user interaction, so it is especially important to ensure that all inputs are valid and expected. Any requests that don’t conform to the API specification must be rejected. Typical best-practice guidelines for input validation apply:
- Treat all parameters, objects, and other input data as untrusted.
- Use built-in validation functionality where available.
- Check the request size and content length and type.
- Use strong typing for API parameters (if supported).
- To prevent SQL injection, avoid building queries manually – use parameterized queries instead.
- Whitelist parameter values and string inputs wherever possible.
- Log all input validation failures to detect credential stuffing attempts.
Why REST API Security Is Important
Rest Api Cheat Sheet 2020
Web APIs are the backbone of modern web and mobile development. They allow applications and services to communicate and exchange data across hardware and software platforms. While other API formats are also still in use (for example SOAP), REST APIs are now the dominant type, accounting for over 80% of all public web APIs. They provide the back end for the majority of mobile applications and IoT devices and allow easy integration across systems and applications.
Because they use the same technologies as web applications, REST APIs can be vulnerable to the same attacks. At the same time, APIs are not designed for manual access, so they can be difficult to test, especially if some endpoints and features are undocumented. API security testing requires accurate automated tools to ensure complete coverage. Netsparker provides full support for REST API vulnerability scanning with a variety of authentication methods and automatic URL rewriting.
See the Netsparker REST API test site documentation for complete technical details and read our full article on scanning REST APIs for vulnerabilities with Netsparker.
