- Sophos Utm Ssh Software
- Sophos Utm Ssh Access
- Sophos XG Firewall: How To Enable SSH Connection
- Sophos Utm Ssh Commands
- Sophos Utm Ssh Proxy
The ‘issue’ with HA configuration
Sophos Utm Ssh Software
Contents 5.2SwaggerUI 14 5.3Confdclient(cc) 15 5.4Config-watch.plx 15 6Examples 16 6.1Packetfilter 16 6.2WebAdminPort 17 7DifferentSophosUTMversions 18. Publishing PowerShell over SSH Using Sophos UTM’s HTML5 VPN Portal Being able to remotely connect to a command line on a server can be extremely useful. Sophos UTM’s HTML5 VPN Portal allows you to provide this without needing to expose the server directly to the Internet or allowing traditional VPN connections.
- Sophos Firewall: How to enable SSH key based authentication KB-000036341 May 23, 2019 0 people found this article helpful. Overview This article describes how to enable SSH key based authentication with the use of public and private keys. This will allow the user to connect with most SSH clients and avoid password prompts when connecting.
- As Sophos UTM is a full layer 7 firewall, it does a lot more than simply allow or drop traffic based on the source or destination like a traditional ‘layer 4’ firewall. Sophos UTM evaluates full HTTP GET requests, determines if the user or subnet has access, if the site is restricted or not, if it contains malware, if the reputation recently dropped, and it can even do HTTPS inspection on.
- Sophos allows remote shell access via SSH. PuTTY is a Windows SSH client, that may be used to sign in to the shell and access the Sophos command line environment remotely. Putty has many options and supports protocols other than SSH, but this article only shows the features necessary to connect to Sophos.
When you set up High Availability (HA) on a Sophos UTM, you simply select the interface your UTMs are connected with as your ‘Sync NIC’, name your device (e.g. Node1), press apply then change the operation mode to Hot Standby (active-passive), like the below.
This is quick and easy to set up, but it’s also easy to forget future diagnostic information e.g. what if I need to get shell access to the SLAVE node? What is the IP address? How on earth are they communicating?

Behind the scenes both actually do get an IP address, more specifically an RFC 2544 address, which is an address space for special IPV4 benchmark testing, reserved by IANA ranging from 198.18.0.0 to 198.19.255.255.
Sophos Utm Ssh Access
In order to truly understand what we are doing we need to first SSH to our MASTER node.
First gain access to the master node
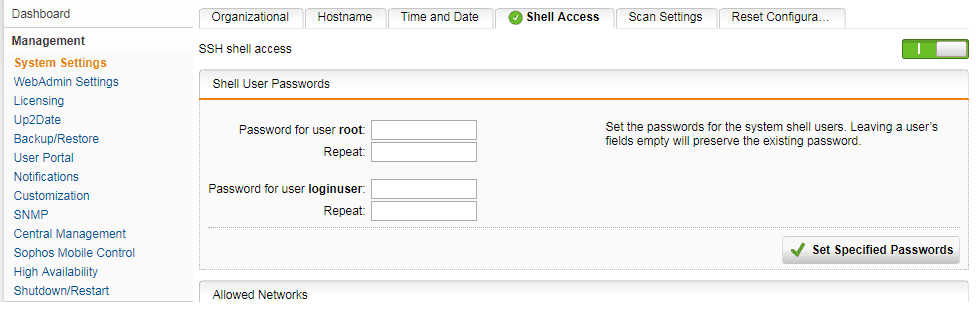
Assuming you have shell access enabled on the MASTER, settings found below, this settings and credentials will replicate to the SLAVE node.
Continue to use your favourite utility for shell access, I’m going to use PuTTy in this example.
NOTE: If this is your first time SSHing into a UTM you need to keep in mind that you first need to log into the ‘loginuser’ before you can elevate your privileges to root (via the SU command).
Now SSH into the MASTER node, you don’t need to gain access to the root account, but if you want to then run the su command when you’re logged in as loginuser.
Now you’re logged into the shell of the MASTER node, we can finally get into the SLAVE node.
Gaining access to the slave node from the master node
There are two powerful commands at our arsenal that help us fully understand what is going on here.
ha_daemon –c status
This will show us the basic status of the HA setup, including the IP address of the MASTER and the IP address of the SLAVE which is assigned across the backup link.
Here we can see that the current mode is HA MASTER, because we are currently logged into the MASTER node.
ha_utils ssh
This is the most useful of commands as this will automatically find the SLAVE’s IP address and will attempt to login as the loginuser via SSH, which will prompt you for credentials.
Sophos XG Firewall: How To Enable SSH Connection
Once you’re logged in, that’s it! You can now check it over.
It’s not often you’re going to need to gain sole access to the slave, being that all changes on the MASTER are replicated to the SLAVE, but on the off chance that you need to you know can have peace of mind that there is a way.
Stay in the loop
Our how-to guides, cyber security advice and productivity tips help businesses stay on track.
Related
Sophos UTM Shell Commands:
Remember:
Direct configuration of Astaro from the shell is unsupported, unless directed to by Astaro Support staff or official documentation.
For paid licenses, modifications done from the shell without direction or sanction may nullify your support agreement.
Run Astaro HTTP proxy database localy
1. ssh to ASG and login with loginuser
2. su – root
3. cc set http sc_local_db [disk][mem][none] (Choose what you prefer)
4. /var/mdw/scripts/httpproxy restart
Websurfing will be extremely slow until the database has downloaded and been put into place. The time is link speed dependent.
View the link speed for the ASG’s interfaces?
‘ifstat’.
Bandwidth usage – IFTOP
Astaro also offers the command ‘iftop’ to see the live traffic and traffic statistics.
One can see the traffic live on an interface for Source Host, Destination Host, and Ports.
The peak and accumulative traffic is also displayed.
Run ‘iftop’
Example:
root # iftop -i eth1
Host display:————————–General:
n – toggle DNS host resolution——P – pause display
s – toggle show source host———h – toggle this help display
d – toggle show destination host—–b – toggle bar graph display
t – cycle line display mode———–B – cycle bar graph average
————————————— T – toggle cummulative line totals
—————————————- Port display: j/k – scroll display
N – toggle service resolution———f – edit filter code
S – toggle show source port———-l – set screen filter
D – toggle show destination port—–L – lin/log scales
p – toggle port display—————- ! – shell command
q – quit
Sorting:
1/2/3 – sort by 1st/2nd/3rd column
< – sort by source name
> – sort by dest name
o – freeze current order
Concurrent Connections:
sysctl -w net.ipv4.netfilter.ip_conntrack_tcp_timeout_establ ished=86400
number of established connections:
less /proc/net/ip_conntrack | grep ESTA | wc -l
1907
number of all connections:
less /proc/net/ip_conntrack | wc -l
3315
number of connections with status WAIT (close_wait):
less /proc/net/ip_conntrack | grep WAIT | wc –l
39
Saving Snapshots of TOP automatically every half hour
create a cron job with,
top -b -n 1 >>/tmp/top-report.txt
An entry for each CPU core, and possibly another if the CPU(s) has hyperthreading:
cat /proc/cpuinfo
stopped and started again the HTTP proxy:
“/var/mdw/scripts/httpproxy stop” and “/var/mdw/scripts/httpproxy start”
Restarting MiddleWare:
service mdw restart
(from root)
Warning: it doesn’t cause a complete reboot, but it does cause an HA failover, interruption of any up/downloads and VoIP calls, etc.
HD
Find what is taking the space type
df –h
df will only tell you how full the disk is.
du will tell you what files/folders are using the most space
I’d recommend:
cd /var/storage
du -sh *
find the offending directories
Sophos Utm Ssh Commands
What kind of CPU
“cat /proc/cpuinfo”?
Determine if the disk is overloaded
vmstat -d 5
or
vmstat -d | head -2 ; vmstat -d 5 | grep hda
if hda is your hard disk; sda for scsi
That should have similar output.
The ‘5’ is 5 second updates.
You’ll have to look at the differences between the lines to figure out how many IO’s you’re getting in those 5 seconds, and whether you’re saturating the disk or not.
See detailed info about your eth:
# ethtool eth1
OR
-mii-diag eth1
webadmin passwd lost
A user may use the following commands to reset the system passwords:
cc
RAW
system_password_reset
Ctrl c
Upon saving the file and exiting, the admin may immediately navigate to WebAdmin and re-specify all passwords for the system accounts of Astaro Security Linux.
DNS Flush cache option missing in V7
the current workaround is to restart the DNS proxy from the command line as root with the following command:
/var/mdw/scripts/named restart
To change version number
login as loginuser
su –
edit /etc/version
save the file
restart the ASG so the new version is displayed in Webadmin dashboard
Change NIC order
login as loginuser
su –
edit /etc/udev/rules.d/70-persistent-net.rules
save the file
restart the ASG so the new order is loaded.
Locked out – How to regain all logins
1) Shutdown the firewall and connect a screen and a keyboard to the firewall
2) Power on the firewall, wait until the GRUB-loader starts and press ‘ESC’
3) Select ‘Astaro Security Gateway 7.2’ (not previous or rescue!)
4) Press ‘e’ to edit and select the 2nd entry
5) Press ‘e’ once again and enter ‘init=/bin/bash’
6) Press ‘ENTER’ and ‘b’ to boot up
7) Now you are able to change the passwords for ‘loginuser’ and ‘root’
8) After that press CTRL + ALT + DEL to reboot the system and wait until you get the login prompt
Reset to factory settings
Login the command-line as ‘loginuser’, afterwards as ‘root’ and enter following commands to restore to factory settings:
1. cc [Press ENTER]
2. RAW [Press ENTER]
3. system_factory_reset [Press ENTER]
The system will automatically shutdown when it’s finished.
Sophos Utm Ssh Proxy

Source: https://community.sophos.com/products/unified-threat-management/f/general-discussion/21326/astaro-useful-shell-commands
Related Posts
